Cybersecurity — the body of knowledge and practices to defend internet-connected devices and products from malicious attacks by hackers, spammers, and cybercriminals — is very important to me. I conduct research into patterns of behavior, tactics, techniques, and procedures used in attacks. These pages and the blog titled "A Pot of Honey" present some of my work in cybersecurity.
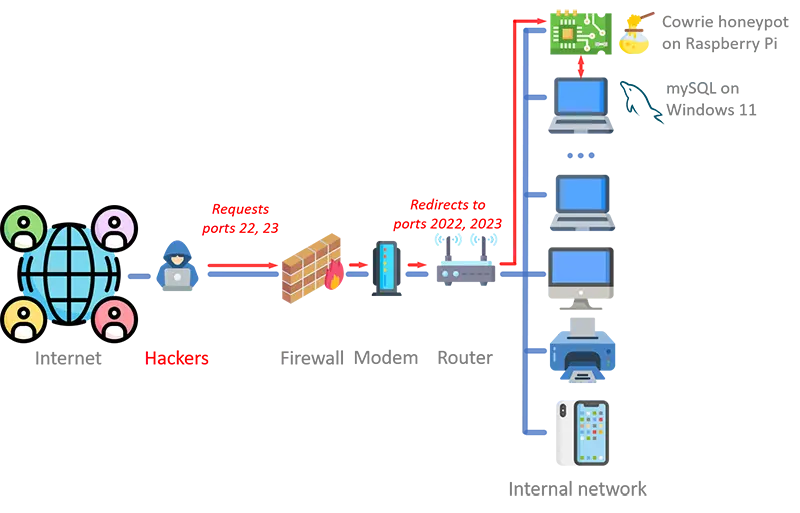
I run honeypots to understand how hackers evolve their attack practices. A honeypot is a controlled and safe network-connected system — typically, but not always, a computer — that is set up as a decoy to lure cyberattackers. In other words, a honeypot is a deception device designed to look like a targetable system for the purpose of attracting attackers. Attack activity against the honeypot is recorded and later analyzed by researchers.
I use Cowrie, a fantastic open-source honeypot capable of collecting attack information over the SSH and Telnet protocols. Cowrie provides an emulation of a Debian-like Linux system. It excels at logging brute-force attacks and interactions performed by attackers on the remote shell.
As, unfortunately, attacks on connected devices are all but ubiquitous, Cowrie generates large amounts of data. I use a MySQL database to host a local copy of the data. I process and analyze the collected data using homegrown tools and APIs developed in Go, Python and the Bash scripting language. As part of the data crunching, I augment the attack data collected by Cowrie with malware information from VirusTotal and IP address information from MaxMind GeoLite2. Both services offer free tiers with reasonable limits on API consumption, so the whole analysis can be performed very cost-effectively. The configuration notes page includes additional details on the set up of my honeypot environment.
I share some of my work on this website and some with the cyber community. See the Results section below for details. For a preview of on-going and upcoming research activitlies, you can take a look at the Future Work section.