Cybersecurity — the body of knowledge and practices to defend internet-connected devices and products from malicious attacks by hackers, spammers, and cybercriminals — is very important to me. I conduct research into patterns of behavior, tactics, techniques, and procedures used in attacks.
I run honeypots to understand how hackers evolve their attack practices. A honeypot is a controlled and safe network-connected system — typically, but not always, a computer — that is set up as a decoy to lure cyberattackers. In other words, a honeypot is a deception device designed to look like a targetable system for the purpose of attracting attackers. Attack activity against the honeypot is recorded and later analyzed by researchers.
I use Cowrie, a fantastic open-source honeypot capable of collecting attack information over the SSH and Telnet protocols. Cowrie provides an emulation of a Debian-like Linux system. It excels at logging brute-force attacks and interactions performed by attackers on the remote shell.
As, unfortunately, attacks on connected devices are all but ubiquitous, Cowrie generates large amounts of data. I use Splunk Free, the free (albeit limited) version of Splunk Enterprise to host a local copy of the data. I process and analyze the collected data using homegrown tools developed in Go, Python and the Bash scripting language. As part of the data crunching, I augment the attack data collected by Cowrie with malware information from VirusTotal and IP address information from MaxMind GeoLite2. Both services offer free tiers with reasonable limits on API consumption, so the whole analysis can be performed very cost-effectively.
Once a day, I report the IP addresses from where unwanted traffic originated to AbusePIDB, a project that aims to make the internet safer by helping systems administrators and webmasters check and report IP addresses involved in malicious activities. My AbuseIPDB contributions can be found here.
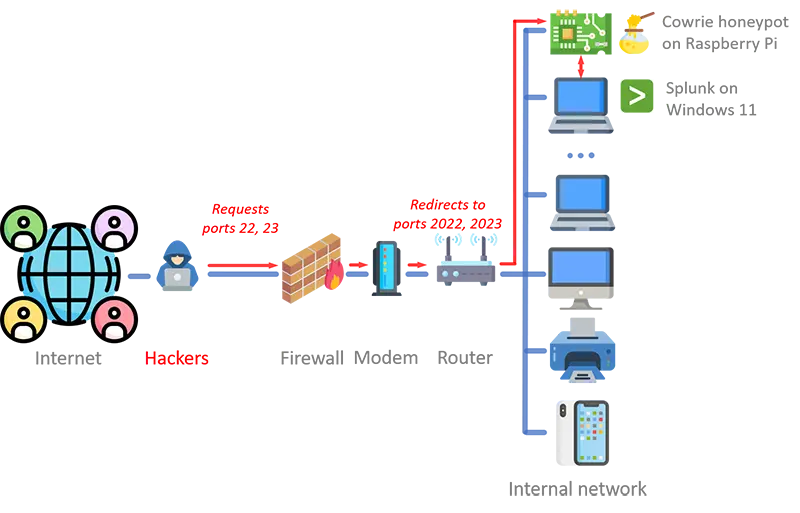
This is a simplified diagram of my setup:
Installing and configuring a Cowrie and Splunk-based honeypot environment is pretty straightforward. Below you can find the steps I took, in case you find the information useful:
Part 1: The Honeypot
I chose Cowrie as the key component of my unwanted traffic detection infrastructure. Cowrie is a superb medium/high interaction honeypot designed to log brute-force attempts and shell interactions launched by attackers over both SSH and Telnet. Cowrie is very popular among both researchers and enthusiasts due to an optimal combination of rich capabilities and ease of use. It is open-source and is backed by an active community led by Michel Oosterhof, the project’s maintainer, creator, and main developer.
1. Choose the honeypot host
You need to start by choosing a Linux system where to install the honeypot. Since Cowrie is very efficient in its resource consumption, I opted for a tiny Raspberry Pi 400 computer as the Cowrie host.
2. Install the system dependencies
Install the system dependencies on the Cowrie host:
$ sudo apt-get install git python3-virtualenv libssl-dev libffi-dev build-essential libpython3-dev python3-minimal authbind virtualenv
3. Create a user account
Installing a user without a password is not an absolute requirement, but it is recommended by the Cowrie authors:
$ sudo adduser --disabled-password cowrie
Adding user 'cowrie' ...
Adding new group 'cowrie' (1002) ...
Adding new user 'cowrie' (1002) with group 'cowrie' ...
Changing the user information for cowrie
Enter the new value, or press ENTER for the default
Full Name []:
Room Number []:
Work Phone []:
Home Phone []:
Other []:
Is the information correct? [Y/n]
$ sudo su - cowrie
4. Get the Cowrie code
Clone the cowrie project from GitHub:
$ git clone http://github.com/cowrie/cowrie
Cloning into 'cowrie'...
remote: Counting objects: 2965, done.
remote: Compressing objects: 100% (1025/1025), done.
remote: Total 2965 (delta 1908), reused 2962 (delta 1905), pack-reused 0
Receiving objects: 100% (2965/2965), 3.41 MiB | 2.57 MiB/s, done.
Resolving deltas: 100% (1908/1908), done.
Checking connectivity... done.
$ cd cowrie
5. Set up a Python virtual environment
Technically speaking, this step is not needed, but it is highly recommended to ensure that package updates on the Cowrie host system will not cause incompatibilities with the honeypot operation:
$ pwd
/home/cowrie/cowrie
$ python -m venv cowrie-env
New python executable in ./cowrie/cowrie-env/bin/python
Installing setuptools, pip, wheel...done.
After you install the virtual environment, activate it and install required packages:
$ source cowrie-env/bin/activate
(cowrie-env) $ python -m pip install --upgrade pip
(cowrie-env) $ python -m pip install --upgrade -r requirements.txt
6. Configure Cowrie
The Cowrie configuration is stored in the cowrie/etc/cowrie.cfg file. To run the honeypot with a standard configuration, there is no need to change anything. By default, Cowrie accepts traffic over SSH. I wanted the honeypot to also accept traffic over Telnet, send the data to Splunk (more on this later), and change the default ports 22 and 23, so I modified the configuration file as follows:
[telnet]
enabled = true
...
[output_splunk]
enabled = true
...
[proxy]
backend_ssh_port = 2022
backend_telnet_port = 2023
I also wanted to change the default user configurations and the list of credentials accepted to login to the remote shell. These changes are made by modifing the cowrie/etc/userdb.txt file. Each line in the file consists of three fields separated by the : character, where:
- Field #1 is the username.
- Field #2 is currently unused and set to
x. - Field #3 is the regular expression that specifies the list of passwords accepted by the user.
As an example, the following settings configure a username admin that accepts all passwords except 1) only numeric characters, 2) the case-sensitive string admin, and 3) the case-insensitive string honeypot:
admin:x:!admin
admin:x:!/^[0-9]+$/
admin:x:!/honeypot/i
admin:x:*
7. Customize Cowrie
Optionally, you can change the look-and-feel of the Cowrie interface to make it look more realistic. A number of files allow you to do that:
- In
cowrie/etc/cowrie.cfg, you can change, for example, the hostname displayed by the shell prompt, the user prompt, the Telnet username and password prompts, the response from theunamecommand, the SSH version printed byssh -V, etc.
hostname = appsrv02
...
prompt = root>
...
telnet_username_prompt_regex = (\n|^)ubuntu login: .*
telnet_password_prompt_regex = .*Password: .*
...
kernel_version = 3.2.0-4-amd64
kernel_build_string = #1 SMP Debian 3.2.68-1+deb7u1
hardware_platform = x86_64
operating_system = GNU/Linux
...
ssh_version = OpenSSH_7.9p1, OpenSSL 1.1.1a 20 Nov 2018
- In
cowrie/honeyfs/etc/issue, you can change the pre-login banner. - In
cowrie/honeyfs/etc/motd, you can change the post-login message. - In
cowrie/honeyfs/proc/cpuinfo, you can change the simulated CPU make-up of the system (e.g., number and type of processors). - In
cowrie/honeyfs/proc/meminfo, you can change the simulated system’s memory allocation and usage. - In
cowrie/honeyfs/proc/version, you can change the Linux kernel andgccversions.
8. Forward listening ports
As we saw above, I configured Cowrie to accept SSH traffic over port 2022 and Telnet traffic over port 2023. In order to preserve the fidelity of the decoy, I opened ports 22 and 23 on the router and forward their traffic to ports 2022 and 2023, respectively, on the system hosting Cowrie.
9. Start Cowrie
Start the honeypot by calling the cowrie/bin/cowrie executable that is part of the Cowrie distribution. An existing virtual environment is preserved if activated, otherwise Cowrie will attempt to load the environment called cowrie-env that we created earlier:
bin/cowrie start
Activating virtualenv "cowrie-env"
Starting cowrie with extra arguments [] ...
Part 2: The Data Repository
I opted for Splunk Enterprise as the warehouse of my Cowrie-generated data because it is very powerful, offers superb API-based data querying and manipulation functionality, can be installed locally, and — best of all — is free if you keep your data volume under 500MB per day. I found it easier to set up and operate than alternatives such as Elasticsearch/OpenSearch and Graylog.
1. Install Splunk
Splunk Free is a free (as in no-cost) version of Splunk Enterprise with limited capabilities. When you first install Splunk Enterpise, it will automatically install an Enterprise Trial license that comes enabled by default. The Splunk Enterprise Trial license is valid for 60 days. The best part is that you can switch to the free license at any time during the trial period. The steps are as follows:
- Navigate to the Splunk Enterprise page.
- If you do not have a Splunk account, create one.
- Log into your Splunk account.
- Under Products, select Free Trials and Downloads, scroll down to Splunk Enterprise, and click the Get My Free Trial button.
- Select the operating system of the machine where you want to install Splunk (I chose Windows), then download the latest version of Splunk Enterprise by clicking on the Download Now button.
- Agree to the Splunk General Terms and click Access Program to start the download.
- Open the downloaded package and follow the installation instructions on your operating system of choice.
2. Switch from Splunk Enterprise to Splunk Free
At any time during your Splunk Enterprise trial, you can switch to the Free license. This is how:
- Login to your administrator account on the web interface of Splunk Enterprise. The default URL is
http://127.0.0.1:8000. - In the upper right-hand corner, navigate to Settings.
- Under System, select Licensing.
- Select Change License Group.
- Select Free license and then click Save.
- On the next screen, select Restart Now for the changes to take effect.
3. Create a Splunk HTTP event collector (HEC)
- Navigate to the web interface of your Splunk instance at
http://127.0.0.1:8000. - In the upper right-hand corner, select Settings.
- Under Data, select Data Inputs.
- Under Local Inputs, click the HTTP Event Collector link.
- Under HTTP Event Collector, click the Global Settings button at the top right of the page.
- Under Edit Global Settings, click Enabled, then click the Save button.
- Go back to Data > Data Inputs.
- Under Local Inputs, click +Add new to the right of HTTP Event Collector.
- Under Add Data, enter a name for your new HEC, then click Next.
- Under Input Settings, click the Create a new index link in the Index section.
- Under New Index, enter
cowrieas the name of your new index, then click Save. - Back under Input Settings, select your newly-created index under Select Allowed Indexes, then click the Review button at the top right of the page.
- Under Review, click the Submit button at the top right of the page.
4. Create a Splunk event collector token
- Navigate to the web interface your Splunk instance at http://127.0.0.1:8000.
- In the upper right-hand corner, select Settings.
- Click the Add Data icon.
- Under Or get data in with the following methods, click Monitor.
- Click HTTP Event Collector.
- Enter a name for the token.
- Click the Next button at the top right of the page.
- Click the Review button at the top right of the page.
- Under Review, click the Submit button at the top right of the page.
- Copy the token value; you will need it in the next step.
5. Configure Cowrie to use the Splunk event collector
We now need to go to back the Cowrie configuration file cowrie/etc/cowrie.cfg and make edits to ensure that Cowrie sends the events it collects to Splunk through the HEC we created earlier. Look for the [output-splunk] section and ensure that it looks like this:
[output-splunk]
enabled = true
url = http://XXX.XXX.XXX.XXX:8088/services/collector/event
token = your_splunk_token
index = cowrie
sourcetype = cowrie
source = cowrie
Replace the XXX.XXX.XXX.XXX part of the url setting with the local IP address on your home network of the system hosting your Splunk instance. Replace your_splunk_token in the token setting with your Splunk token. Leave the index, sourcetype, and source settings set to their cowrie default.
6. Verify that everything works
If all the above configuration steps went well, you should now have Cowrie connected to Splunk. Start Cowrie on the system where it was installed (Raspberry Pi in my case) and make sure that your Splunk service is running on the system where you installed it; mine runs on Windows 11. Assuming that your honeypot is being attacked — a very safe bet — you should see nicely formatted events on your Splunk instance. To view them, select Apps > Search & Reporting from your Splunk web interface and enter the following in the New Search text field:
index=cowrie
That’s all. Happy threat hunting!
Leave a Reply